In previous posts, I have discussed using social engineering to persuade an unwary or untrained user to click a link, open an attachment, or provide information.
What needs to be asked is, “how?”
Suppose they are trying an unsophisticated attack to steal passwords or get an employee to make purchases on the attacker’s behalf. In that case, they simply exploit an employee’s willingness to be helpful.
If they are trying to get you to click a link or open a fake or booby-trapped attachment, then often, the attacker is attempting to exploit weaknesses in the employee’s computer. Gone are the days when attackers would email malware. Email protection software is adept at spotting this and quarantining the email.
Instead, attackers use a “living off the land” technique where they will try to use parts of the operating system or web browser to do the work for them.
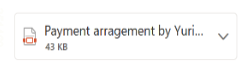
One example is fake email attachments. These are image files made to look like an attachment (e.g., PDF or Docx file) that contain embedded URLs (see below). When you attempt to open them, they reach out to the internet to download and execute commands or malware, even downloading a PDF file and opening it to avoid raising suspicion.
For many years, web browsers have conveniently allowed users to store credentials. This has the added benefit of allowing different credentials for different websites, which is a recommended security best practice. However, suppose an attacker can persuade an employee to click a link that installs a malicious browser add-in. In that case, it can be leveraged to steal those credentials, and the attacker can impersonate the employee. Even without the add-in, a “lookalike link” (subtly different from a real URL, as shown below) can direct a distracted employee to a server owned by the attacker. After clicking the “lookalike link,” it forwards all the information to the actual target to avoid suspicion but intercepts information in the process. This is called a man-in-the-middle attack.
Can you spot the fake URL?
1inked-in.com
linked-in.com
linked-ln.com
Multi-Factor Authentication
“Ahh, but we use MFA,” I hear you say. Unfortunately, a compromised browser can be used to steal MFA codes as they are typed or the authentication cookie that is created after authentication has been successfully completed.
Not all attacks focus on web browsers – others will target the operating system. Most operating systems have a command line system that is used for automation purposes. Attackers can leverage this when a user opens a booby-trapped attachment or clicks on a malicious link that requests your computer reach out to the internet and download malware. This malware doesn’t even have to install itself on a disk; it could try to fly under the radar and run in memory. This makes it less likely to be spotted by antivirus solutions.
If a computer is rebooted, won’t the malware disappear?
Absolutely, because memory resident malware isn’t the end goal. This malware can steal user credentials, try using their privilege to escalate its own, and once a foothold is gained, maintain access in various ways (scheduled tasks, scripts, remote access tools).
How many users insist they should be administrators on their computers?
If they are an administrator, then the malware can use that account to create accounts that the attacker can use without raising suspicion. Or, they can reach out to the network, find accounts belonging to other users, and steal those. Using these accounts, they can stealthily steal patient data, company data, or install ransomware that will encrypt all your data (and backups) and extort your ASC (pay up or else).
Good security software has a vital role to play. In addition to examining files written to disk, some can examine malicious URLs and provide ransomware protection. However, a new class of security software looks at what actions the software or application is being asked to perform, and if it seems suspicious, it will generate alerts. This new class of software is called EDR (Endpoint Detection and Response) or XDR (eXtended Detection and Response). A Managed XDR vendor is best for you unless your ASC has a dedicated security team of trained professionals. They will request all devices have an agent installed that collects and reports suspicious activity. The XDR vendor will perform an analysis 24×7, notify your ASC if they spot something amiss, and ask what steps you would like them to take. Next steps might include anything from clean-up to forensic analysis. No system is perfect, but with the right partner, the likelihood of a malicious actor remaining undetected in your network is reduced.
What should an ASC employee do to help protect their organization, their patient’s privacy, and themselves?
- Do not store credentials in a web browser; instead, use a highly-rated password manager (some will have add-ins for popular web browsers).
- Always scrutinize URLs before clicking them. If in doubt, copy and paste into a text editor, or use a search engine to go to the legitimate site without clicking the emailed/text message link.
- Be wary of attachments. If it is unexpected, do not open it. If unsure, reach out to the organization in question using an officially published number (not the ones in the email, as they can be fake) and verify its authenticity.
- Do not give users computer administrator accounts for everyday access.
- Install and keep up-to-date antivirus software.
- Deploy a Managed XDR platform or MSSP (Managed security service provider).
Don’t miss out on the good stuff – Subscribe to HST’s Blog & Podcast!
Every month we’ll email you our newest podcast episodes and articles. No fluff – just helpful content delivered right to your inbox.

